[ Chapter 1 ] [ Chapter 2 ] [ Chapter 3 ] [ Chapter 4 ] [ Chapter 5 ] [ Chapter 6 ] [ Chapter 7 ] [ Index ]
Chapter 1 - Introduction
Introduction
Mobile or nomadic computing
Wireless Ubiquitous Personal
Architecture
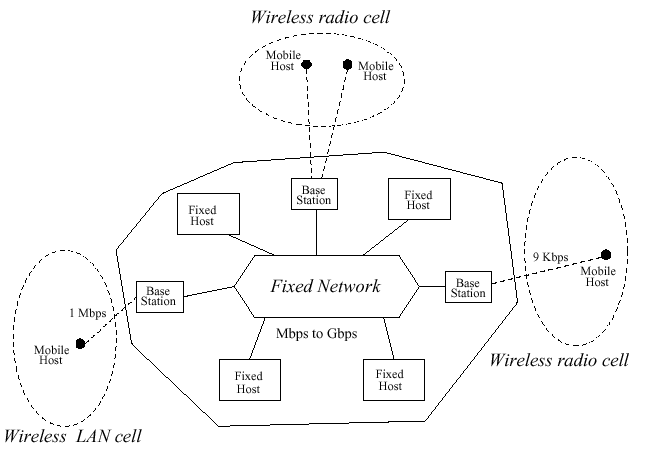
Issues
Key Issues: Mobility, Wireless Communications, and Portability [7, 2, 4, 1]
The location of mobile elements and therefore their point of attachment to the fixed
network change as they move. The consequences of mobility are numerous.
- The configuration of a system that includes mobile elements is not static. Thus,
1.In designing distributed algorithms, we can no more rely on a fixed topology.
2.The center of activity, the system load, and locality change dynamically.
- Location management
1.The search cost to locate mobile elements is added to the cost of each communication involving them.
2.Efficient data structures, algorithms, and query execution plans must be devised for representing, managing, and querying the location of mobile elements, which is a fast changing data.
- Heterogeneity
1.Connectivity becomes highly variant in performance and reliability. For instance, outdoors, a mobile client may have to rely on low and width networks, while inside a building it may be offered reliable high-bandwidth connectivity or even operates connected via wireline connections. Moreover, there may be areas with no adequate coverage resulting in disconnections of various durations.
2.The number of devices in a network cell changes with time, and so do both the load at the base station and bandwidth availability.
3.There may be also variability in the provision of specific services, such as in the type of available printers or weather reports.
4.The resources available to a mobile element vary, for example, a docked computer has more memory or is equipped with a larger screen.
Mobility also raises very important security and authentication issues.
- (Weak and Intermittent Connectivity)
Wireless networks are more expensive, offer less bandwidth, and are less reliable than wireline networks. Wireless communications
face many obstacles because the surrounding environment interacts with the signal. Thus, while the growth in wired network bandwidth has been tremendous (in current technology Ethernet provides 10 Mbps, FDDI 100 Mbps
and ATM 155 Mbps), products for wireless communication achieve only 19 Kbps for packet radio communications, and 9-14 Kbps for cellular telephony. The typical bandwidth of wireless LANs ranges from 250 Kbps to 2 Mbps and it is
expected to increase to 10 Mbps Since the bandwidth is
divided among the users sharing a cell, the deliverable bandwidth per user is even lower. For radio transmission the error rate is so high that the effective bandwidth is limited to less than 10 Kbps Thus, bandwidth is a scarce resource.
Furthermore, data transmission over the air is currently monetarily expensive Mobile elements may voluntary operate disconnected.
- (Variant Connectivity)
- (Broadcast Facility)
- (Tarrifs)
Wireless technologies vary on the degree of bandwidth and reliability they provide.
There is a high bandwidth broadcast channel from the base station to all mobile clients in its cell.
For some networks (e.g., in cellular telephones), network access is charged per connection-time, while for others (e.g., in packet radio), it is charged per message (packet).
Portability of Mobile Elements
- Mobile elements are resource poor when compared to static elements.
Mobile elements must be light and small to be easily carried around. Such considerations, in conjunction with a given cost and level of technology, will keep mobile
elements having less resources than static elements, including memory, screen size and disk capacity. This results in an asymmetry between static and mobile elements.
- Mobile elements rely on battery.
Even with advances in battery technology, this concern will not cease to exist.
Concern for power consumption must span various levels in hardware and software design.
Mobile elements are easier to be accidentally damaged, stolen, or lost.
Thus, they are less secure and reliable than static elements.
Summary
Characteristics of mobile elements
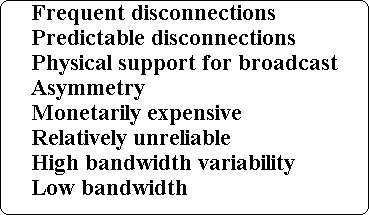
Characteristics of wireless communications

Network Disconnections
Voluntary or forced Predictable or sudden. Short disconnections and long
Disconnected operation
An Example
Satya's vision of a hypothetical trip in the year 2000 [8]: Imagine you are sitting at your office working on a report stored
in a shared file system. Soon, it is time to leave. You use your machine to call for a taxi. You continue working as necessary files are prefetched in your notebook. When the taxi arrives, you pick up your notebook and leave. On the ride to the airport, you continue working. Your notebook recognizes that it is no longer on a LAN, but continues communicating via a cellular modem. There are some gaps in communication, but they remain
completely transparent to you. You finish editing, save the file, and send email to your coauthor. At the airport, while waiting for boarding, you use your notebook for web - browsing. While on board, you start working on your
slides. Although each seat is equipped with an outlet for air-to-ground telephone service, your notebook discovers that telephone charges are very high. Thus, it wisely decides to let you operate disconnected and defer all
communication. Your requests for some old figures are also postponed for later service. When you arrive at your hotel room, your notebook discovers that the hotel's late-night telephone charges are low. It therefore
propagates the changes you have made so far, fetches new versions of the files you had cached, and picks up your mail and the figures you have requested. Next morning, you present your talk. Your notebook senses the
presence of a large wall-sized display and shows your slides on it through an infrared link. Since your talk is about a new piece of user-interface software, your are able to give a live demo of it using your notebook.
Next day, you decide to do some sightseeing and rent a car. The car is provided with a navigating interactive screen map that you use to tour the city. The map is intelligent enough to avoid traffic jams by listening to
periodically broadcasted traffic information. When you arrive, you grab your notebook that downloads a guided tour of the site. As you walk around, a video describing the features of the site is seen and the accompanying commentary
is heard. Before leaving, you purchase a t-shirt at the gift shop. The store clerk obtains your travel itinerary from your notebook and arranges for your duty free purchase to be delivered to the correct gate. Next
morning you take the metro to the airport. On the metro, you use your notebook to watch CNN. From time to time, as the train goes through regions of poor reception, the displayed image degenerates from full-motion to slow-scan
black and white. When you arrive at the airport, you pick up your gift at the gate. During the flight you can relax: your notebook has been recording your purchases and is now automatically preparing an expense report to be
transmitted to your secretary for reimbursement.
[1] R. Alonso and H. F. Korth. Database System Issues in Nomadic Computing. In Proceedings of the 1993 SIGMOD Conference, Washington, D.C., May 1993. [2] G. H. Forman and J.
Zahorjan. The Challenges of Mobile Computing. IEEE Computer, 27(6): 38-47, April 1994. [3] D. Hayden. The New Age of Wireless. Mobile Office, May 1992. [4] T. Imielinksi and B. R. Badrinath. Wireless
Mobile Computing: Challenges in Data Management. Communications of the ACM, 37(10), October 1994. [5] C. J. Mathias. New LAN Gear Snaps Unseen Desktop Chains. Data Communications, 23(5): 75-80, March
1994. [6] K. Miller. Cellular Essentials for Wireless Data Transmission. Data Communications, 23(5): 61-67, March 1994. [7] M. Satyanarayanan. Fundamental Challenges in Mobile Computing. In Proceedings of
the 15th ACM Symposium on Principles of Distributed Computing, Philadelphia, PA, May 1996. [8] M. Satyanarayanan. Mobile Information Access. IEEE Personal Communications, 3(1), February 1996.
[ Chapter 1 ] [ Chapter 2 ] [ Chapter 3 ] [ Chapter 4 ] [ Chapter 5 ] [ Chapter 6 ] [ Chapter 7 ] [ Index ]
[EPL651] [Course Contact] [Schedule & Readings] [Assignments] [Resources] [What's New]